RHEL and CentOS operating systems provide the SELinux security feature by default. The SELinux is enabled by default but in some cases, we may need to disable SELinux. This tutorial explains how to disable CentOS7, CentOS8, and RHEL SELinux.
SELinux Modes
Before disabling SELinux for CentOS we should know the SELinux modes. SELinux provides the following 3 modes where the Disabled is the mode we want to activate.
- Enforcing mode is the most restrictive mode where every SELinux policy and rule is implemented without exception.
- Permissive mode is used to log denied actions according to rules and policies but does not deny any actions and only logs.
- Disabled is the mode where no policy or rule is executed or logged.
Check SELinux Status In CentOS
Before disabling the SELinux for CentOS we can print the current configuration of the SELinux. The sestatus command simply displayed SELinux status. The sestatus command provides a lot of details about the SELinux status like status, mount point, root directory, current mode, policy MLS status, memory protection checking, and max kernel policy version.
$ sestatusSELinux status: enabled SELinuxfs mount: /sys/fs/selinux SELinux root directory: /etc/selinux Loaded policy name: targeted Current mode: enforcing Mode from config file: enforcing Policy MLS status: enabled Policy deny_unknown status: allowed Memory protection checking: actual (secure) Max kernel policy version: 33
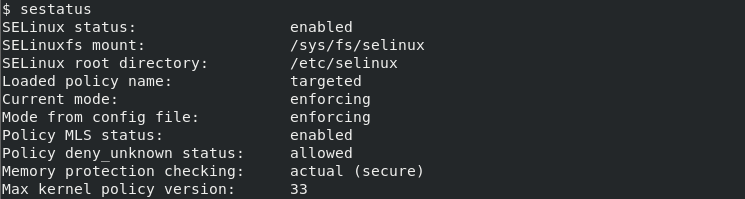
Alternatively, the getenforce command can be also used to print the current SELinux enforcement status for the CentOS and RHEL.
$ getenforceDisable SELinux In CentOS (Temporarily)
The setenforce command is used to change the SELinux mode or status in CentOS. We can use the setenforce command in order to disable SELinux. The setenforce command requires 0 as parameter to disable SELinux. The setenforce command changes SELinux mode temporarily and this configuration is lost if the system is rebooted.
$ setenforce 0Disable SELinux In CentOS (Permanently)
The SELinux configuration is stored in /etc/selinux/config . The configuration file content is like below where the SELINUX line should be set disabled to disable SELinux. This configuration is permanent and event the system reboots the SELinux stays as disabled.
# This file controls the state of SELinux on the system.
# SELINUX= can take one of these three values:
# enforcing - SELinux security policy is enforced.
# permissive - SELinux prints warnings instead of enforcing.
# disabled - No SELinux policy is loaded.
SELINUX=disabled
# SELINUXTYPE= can take one of these three values:
# targeted - Targeted processes are protected,
# minimum - Modification of targeted policy. Only selected processes are protected.
# mls - Multi Level Security protection.
SELINUXTYPE=targeted
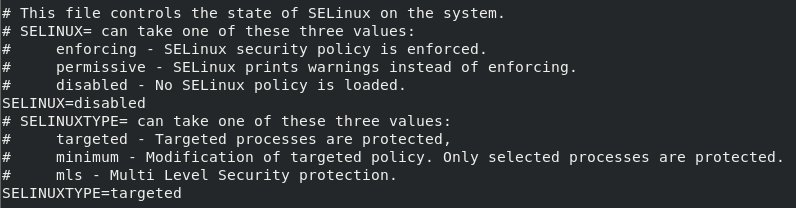
In order to make the configuration effective reboot the system with the following command.
$ sudo reboot